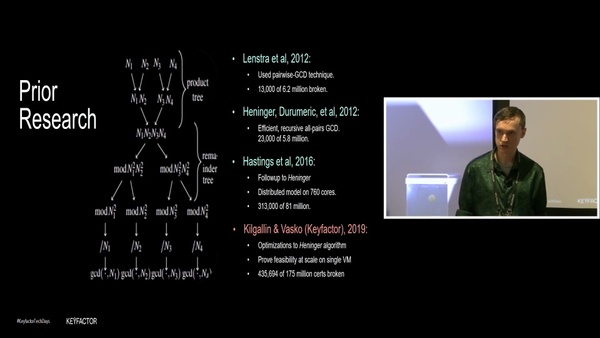
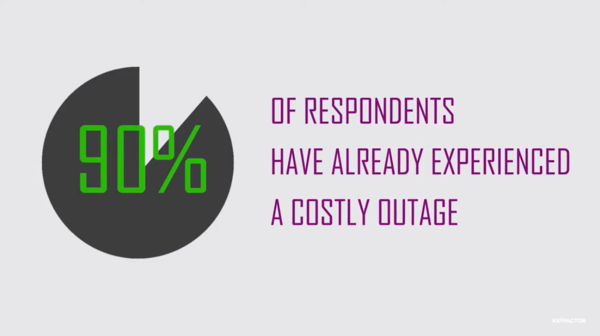
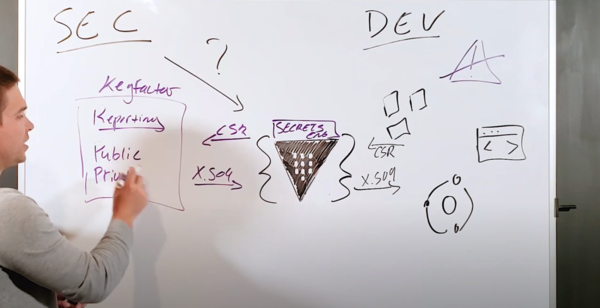
Filters

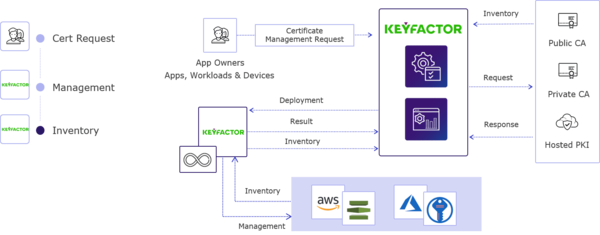
Keymaster
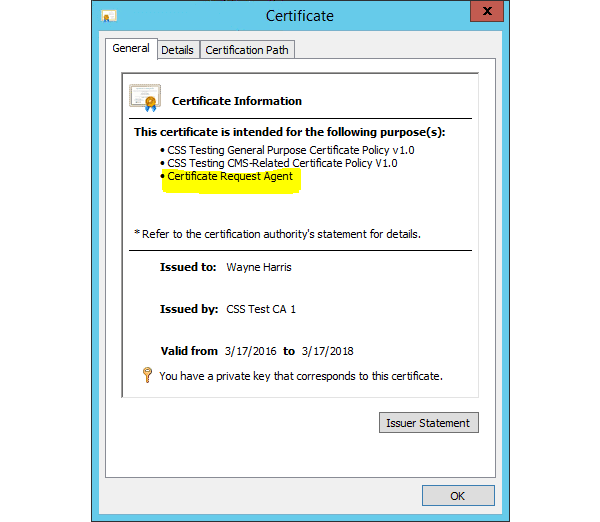
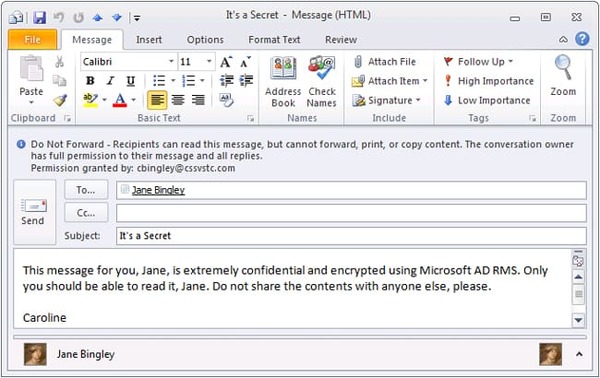
Navigating the Transition to FIPS-140-3 – Upgrading Your HSMs and Preparing for the Future

Presentation
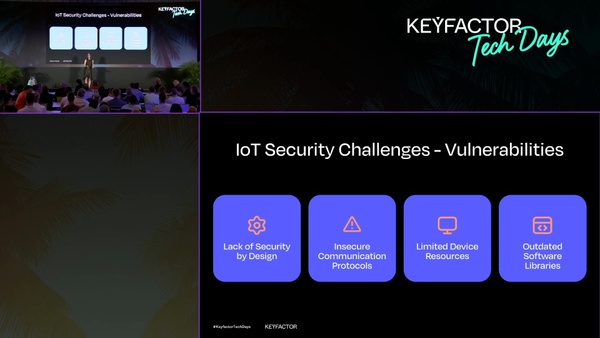
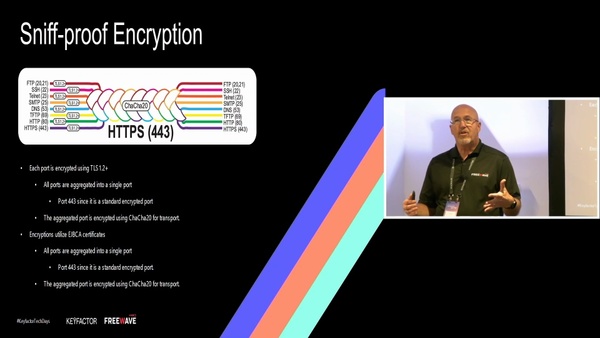
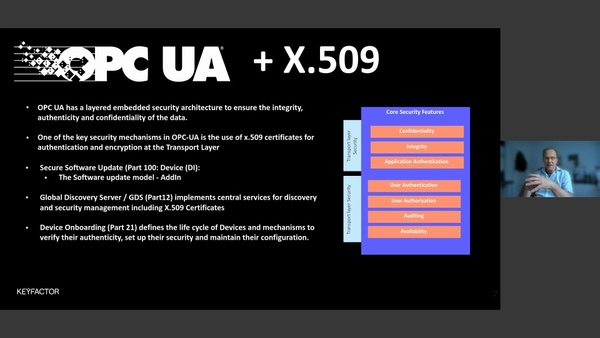
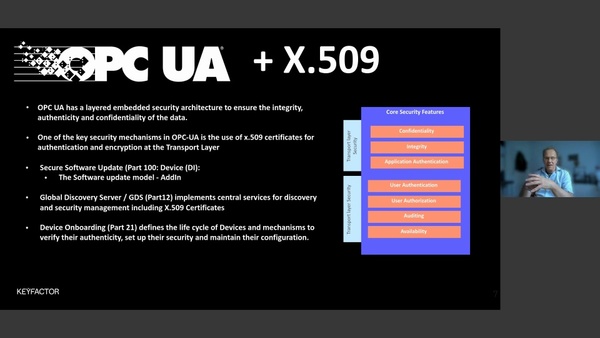
TECHSynergy in Secure IoT Deployments - Secure Boot, Secure OTA, and Security In OPC/UA

Presentation
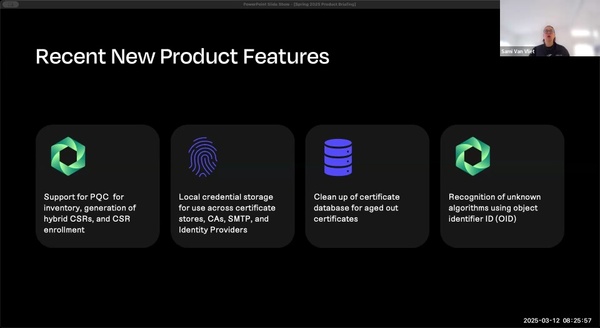
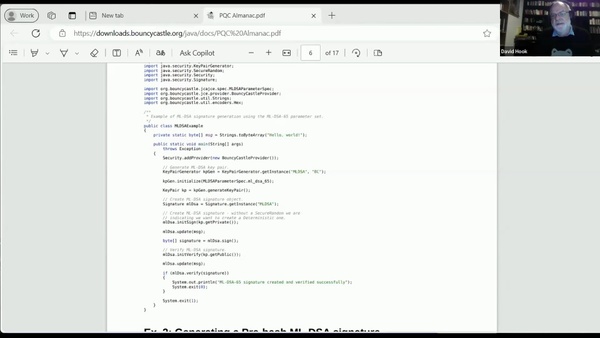
PQC Crypto Agility and Hybrid Certificates, Different Formats, and Migration Strategies

See more...
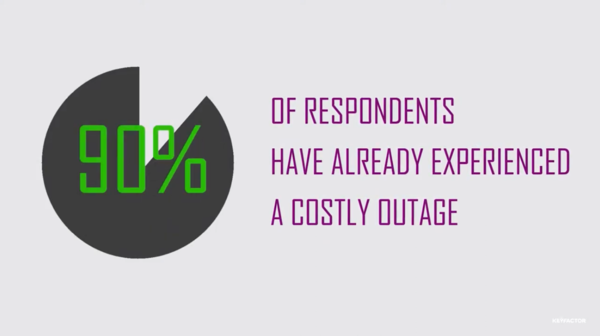
Why COVID-19 Budget Cuts Shouldn’t Include IT Security Spend – Expert Source | Keyfactor

See more...
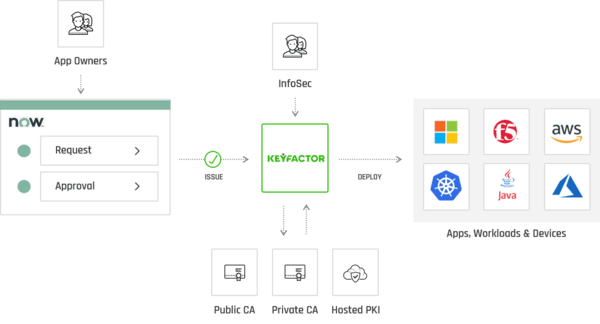
Build or buy: What to consider when deploying on-premise or cloud-based PKI. | Keyfactor

See more...
Keyfactor Wins 2024 Fortress Cyber Security Award for Third Consecutive Year | Keyfactor

See more...
Keyfactor Opens France Office to Further Accelerate Regional Market Traction | Keyfactor

See more...
Keyfactor to Exhibit and Present on Healthcare Security Solutions at HIMSS19 | Keyfactor

See more...
Keyfactor Launches Partner Network, Announces Channel Leadership Appointment | Keyfactor

See more...
Keyfactor and Thales Address Code Signing Cyber-Attacks Targeting Businesses | Keyfactor

See more...
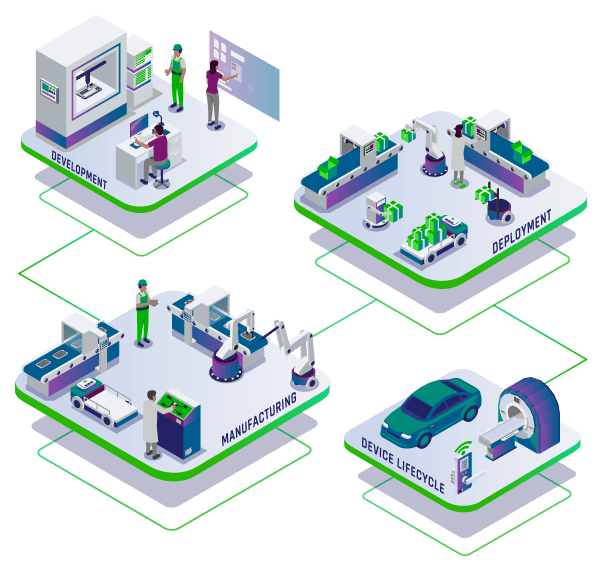
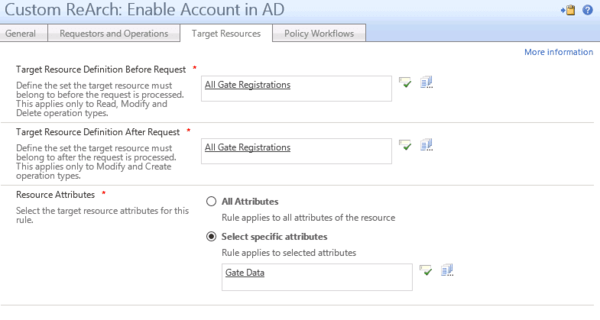
PKI and Certificates for Industrial IoT: What They Are and Why You Need Them | Keyfactor

See more...
Key Takeaways From the PKI Consortium’s Post-Quantum Cryptography Conference | Keyfactor

See more...
Webinar Recap - How PKI, Crypto and Machines Make the Digital World Go Round | Keyfactor

See more...
Organizational-wide Visibility is Crucial to Protect Against Today’s Threats | Keyfactor